Testing+ Results
Internal & External Penetration Testing
With the explosion of cyberattacks in the resent years, it has become critical that companies protect their business critical data by identifying vulnerabilities in their systems. Cyber threats are not only becoming more frequent but also more sophisticated.
As the frequency and severity of attacks increase, the need for cyber security testing dramatically increases. Penetration testing is an invaluable process that can identify vulnerabilities and issues that traditional IT security tools may not pick up. The most cost-effective way to reduce your risk of cyber-attacks is through penetration testing.

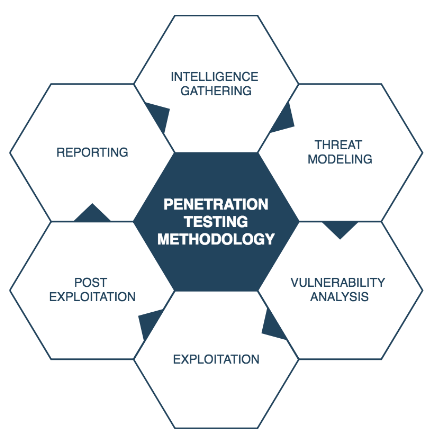
3 Reasons Why Penetration Testing Is Important
The need For A Secure Infrastructure
Penetration testing exploits the weak spots in applications or the network which then can be easily infiltrated by a cyber criminal.
Effective Security Planning & Awareness
Effective Security Planning & Awareness - The security of the organization’s data is critical to operational effectiveness. However, there is always the risk of being compromised by a disgruntled employee, or by hackers. In either case, it’s important to be prepared and understand your security weaknesses.
Customer Trust & Reputation
A business’s reputation can be easily destroyed. Simple news about a company’s data leak can destroy all the confidence you have built with your clients over the years.

We Can Help!
Internal Penetration Testing
The goal of our Internal Penetration Test is to assess the ability of an unprivileged user, or attacker, that has gained initial access to the organizations network, and to uncover any current or potential vulnerabilities.
Our team offers comprehensive network penetration testing services that include environmental reconnaissance, privileges escalation, lateral movement, and vulnerability exploitation. We use compromised systems and services to exploit other systems in the customer's environment in order to test the depth of their network defenses and accomplish pre-defined objectives. These tests are conducted with the utmost care and security protocols are followed throughout.
Talk To Us Today
Ensuring that your perimeter and internal defenses' are working properly, or exposing any network vulnerabilities to keep the cyber criminals from infiltrating your network is critical to your Cyber Security strategies. Don’t wait until it’s too late. Contact us NOW!
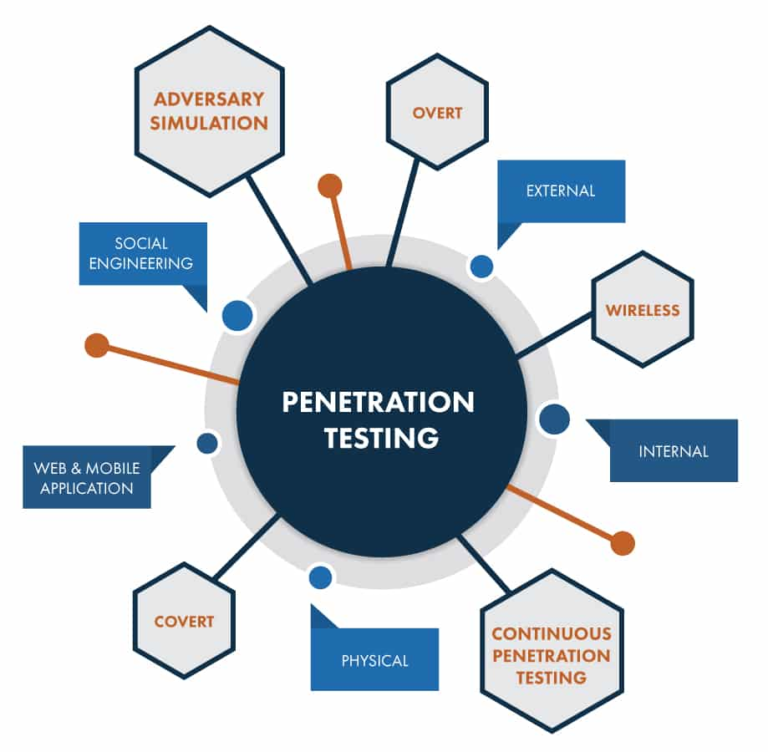
Strengthen + Ensure security
External Penetration Testing
The goal of the External Penetration Test is to assess the security strength of Internet accessible systems, services, and applications. The team will enumerate all accessible systems and services, which may include significant, publicly accessible cloud infrastructure like Office 365 or G Suite, within the defined scope parameters. We will then proceed to identify and validate vulnerable or misconfigured systems, services, and applications.
Internally Developed Tools And Scripts
We attempt to accomplish the pre-defined objectives by any in-scope means not explicitly stated as off limits or potentially harmful to the environment. These objectives could include, but are not limited to; compromise of the domain, theft of email, or proof of access to sensitive data, such as payroll, intellectual property, Personally Identifiable Information (PII), or Personal Health Information (PHI).

Benefits :
- Discover if your critical assets are at risk
Identify and mitigate complex security - Vulnerabilities before an attacker exploits them
- Understand how the most sophisticated attackers operate based on intelligence gained from our years performing incident response
- Attain realistic findings and comprehensive recommendations
Deliverables :
- High level executive summary report
- Technical documentation that allows you to recreate our findings
- Fact-based risk analysis to validate results
- Tactical recommendations for immediate improvement
- Strategic recommendations for long-term improvement
